
New Tinynuke variant with a DGA in the wild
Summary
Tinynuke, or Nukebot malware, is a trojan able to perform man in the browser attacks against modern web browsers and equipped with the most common features needed by a bank trojan (e.g. Webinjects, Socks proxy, VNC, Remote command execution). This malware was in the spotlight in 2017 after the complete bot source code was leaked in March by someone claiming to be the author of the malware.
The leaked source contained a fully working bot, builder and botnet control panel and, as we have seen in past, leaks of working malware usually lead to that malware being used increasingly and new variants and adaptations of it start to emerge.
We at Bitsight constantly monitor the internet for new threats that may affect the security of organizations worldwide. A few months ago we first noticed an unknown DGA showing up in our network traffic analysis system that we could not identify. After some research we managed to identify the malware behind it, and found a malware operation targeting users in the United Kingdom and Canada using a new variant of Tinynuke with some improvements, such as the use of a DGA (Domain Generation Algorithm) for it’s command and control channel or asymmetric cryptography for C2 authentication.
Malware distribution
The malware is being distributed through fake websites (fake product website or fake blogs) promoted through social networking and advertising, that contain links to malicious software installers.
The following is an example of one of these websites being used to distribute a trojanized pdf reader software installer.
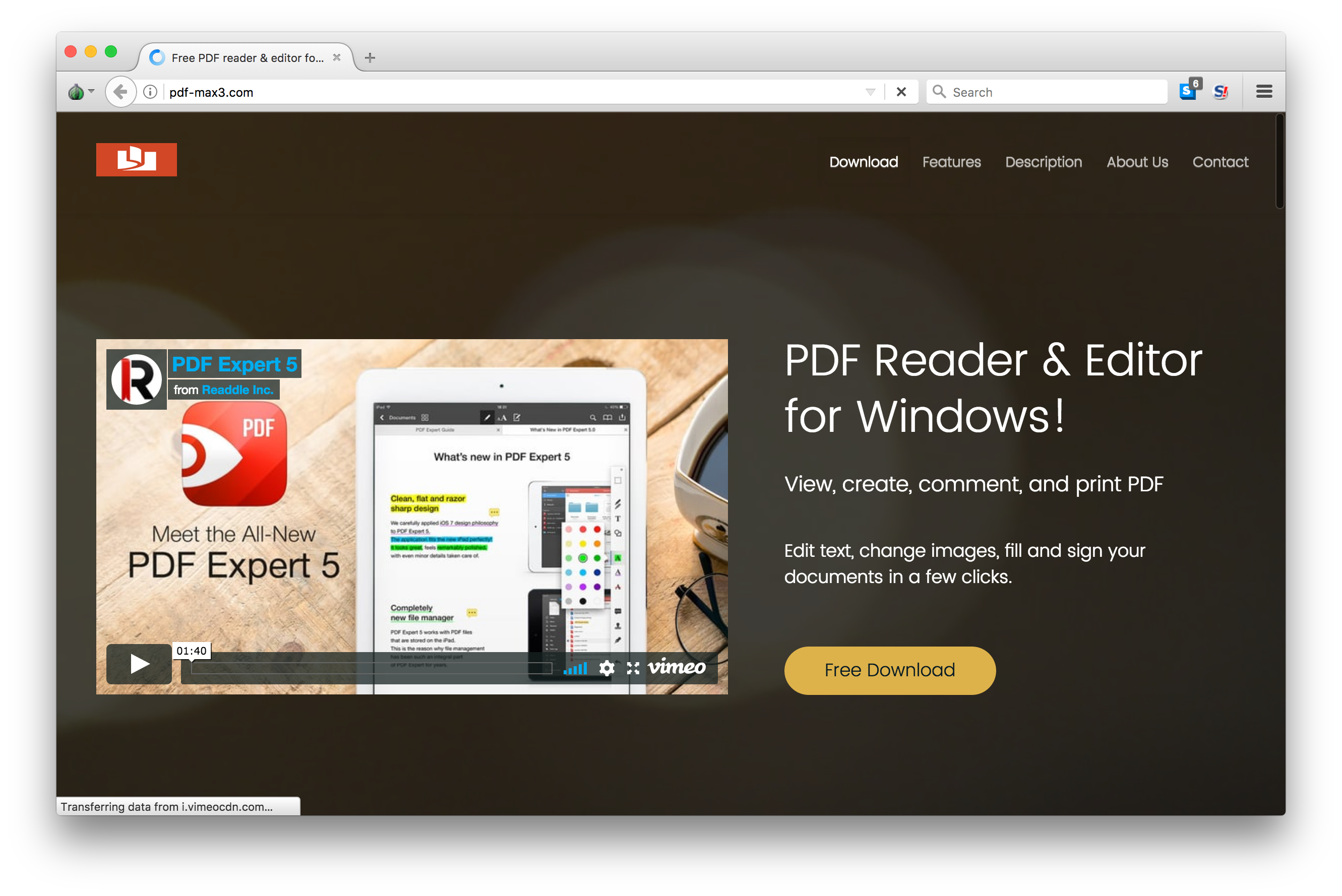
Another interesting example is a fake cryptocurrency security advice blog that was set-up to make available a set of fake installers of known tools that can be used to make a PC more secure. This fake blog was reported to be promoted through facebook advertising by a user who found it suspicious. He wrote about it on his blog (see references). The following image shows this website:
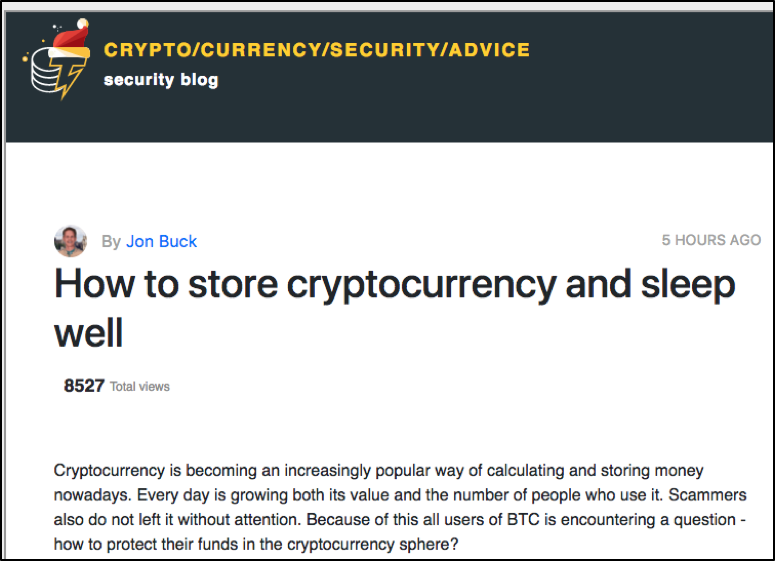
The software installers contain both the trojan and a legitimate software installer and are, in most cases, digitally signed by a company called “AGM 1980 Limited” with a valid certificate signed by Comodo CA.
Once the user executes the fake installer:
- Requests administrative privileges to continue with the installation;
- Performs several checks to verify if it is running on a sandboxed environment (e.g. number of CPU’s, Installed RAM, Virtualization software);
- If the installer is running on a sandbox it proceeds with the legitimate tool installer and does not install the malware;
- If the installer is not on a sandbox it installs the malware and then proceeds with the legitimate installer;
After the trojan is installed and running, the user’s system is compromised and it’s data at risk.
Affected countries
In order to gather some data about the geographies targeted by the malware we have sinkholed it’s DGA domains and observed that there are currently at least 2 different botnets, each using a different TLD on the DGA and each targeting users in a specific country. In particular, one botnet seems to be targeting users in Canada and other users in the United Kingdom.
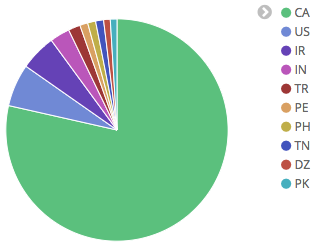
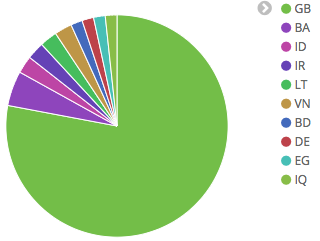
Webinjects and targets
Looking at the webinject configuration we found that besides a few test injects there were also specific injects for two targets. Amazon and Lloyds bank, as shown in the following excerpt (the full webinjects are listed in the IOC’s section):
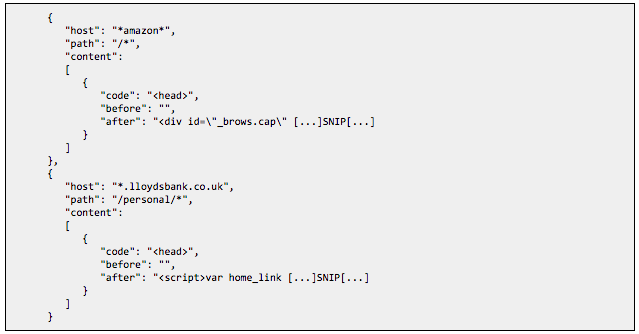
These injects include additional javascript from domains that were registered using the same email address that was used to register the hardcoded domains and the active DGA domains, indicating that these are possibly being developed by the same person or group.
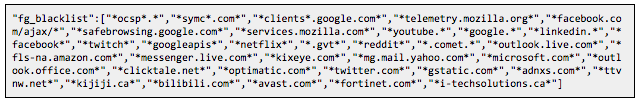
It is also worth noting that besides these two webinjects, the normal bot behaviour is to collect HTTP POST request data on IE, Firefox and Chrome for all hosts not listed in the fg_blacklist object in the config. The following blacklist was found active:
Malware variant
The malware is mostly the same as the TinyNuke bot that was leaked. However, there are some new features, of which the following are the most relevant:
DGAPerhaps the most interesting modification is the introduction of a DGA. This DGA increases the resiliency of the botnet against takedown requests and is triggered when the hardcoded C2 is unreachable.
Its implementation is very simple, it consists of the md5 of a number concatenated with the current day. The following is an example implementation of the DGA in python:
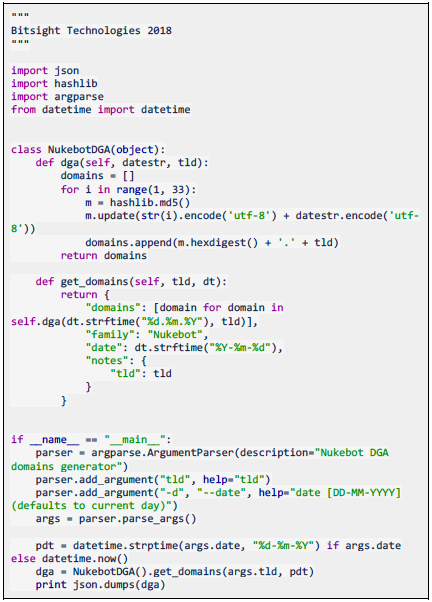
The bot uses asymmetric cryptography to authenticate the C2, as a measure to prevent botnet takeover. To do this, the malware:
- Generates a random 8 byte long string and calculates it’s md5 value;
- Encrypts this value using the C2 RSA Public key that is hard coded on the bot;
- Checks if the md5 of the send value is present in the response to the ping command;
- If it is, the malware stores this C2 as the active C2 in a global variable and communicates with it directly on further interactions;
The following public key was found in use:

The bot has been modified to support what appears to be a proxy layer between the C2 and the infected bots. The HTTP requests now have the following format:
![]()
The new version includes a few self protection features not present in the leaked source. These are the same that exist in the fake software installers used to drop the malware:
- Check for sandbox related usernames by looking for the strings:
![]()
- Check physical memory on the device is higher than 1Gb;
- Check if the system has more than one CPU;
- Check if the Sleep command is being bypassed by calling Sleep and checking if the process actually sleeps;
- Check for VMWare tools registry keys;
- Check for VirtualBox guest additions files;
- Check if the user is connected through remote desktop;
Conclusion
This is an interesting evolution on the TinyNuke malware family and we will continue to monitor this threat as it progresses.
References
- https://securingtomorrow.mcafee.com/business/tinynuke-may-ticking-time-bomb/
- https://securelist.com/the-nukebot-banking-trojan-from-rough-drafts-to-real-threats/78957/
- https://krebsonsecurity.com/2017/04/self-proclaimed-nuclear-bot-author-weighs-u-s-job-offer/
- https://securityintelligence.com/the-nukebot-trojan-a-bruised-ego-and-a-surprising-source-code-leak/
- https://rootvideochannel.blogspot.pt/2017/12/suspicious-website-cryptocurrencysecuri.html
IOC
e2a3bf38387c751bcb971f0234a7a89f74f2b7c807bf6503b4b58fcfbaafa1d6