We’ve compiled 16 valuable, easy-to-understand cybersecurity and cyber risk KPIs that can be integrated into a dashboard for any member of an organization who wants to become more aware of cyber risk.

There are many different metrics that the CISO or CIO collects to measure the performance and effectiveness of its cybersecurity program. But only a select number of these metrics hold enough weight to be reported to the C-suite. The security metrics and measurements that make it to the boardroom should be presented in a language the Board understands, and should speak directly to whether the organization is taking the right steps toward security.
Below, we’ve outlined four commonly used metrics in the area of security you may want to consider for reporting cyber security to your board:
1. Company vs. Peer Performance
The number one metric for board-level reporting today is how your organization’s performance compares to the peers in your sector. This is easily digestible, visually appealing, and highly compelling, which makes it a top choice for a board presentation.
You can gather this metric a number of ways. The example below is a screenshot from Bitsight Security Ratings, which allows you to easily compare your performance to a number of your competitors over a period of time. The image below shows the graphic you could generate for your board with the click of a button.
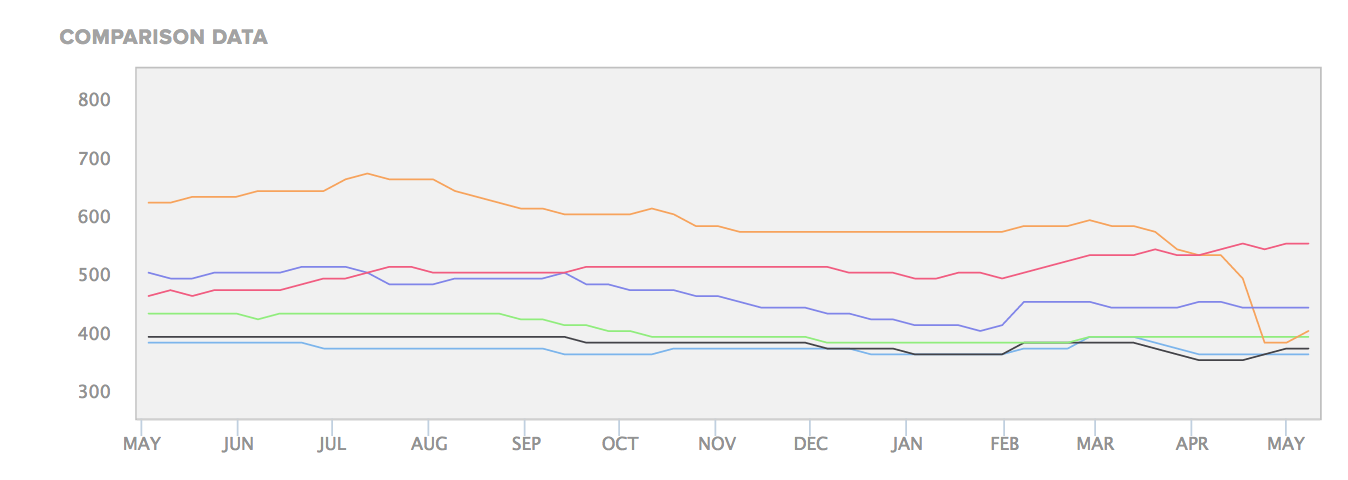
2. How quickly can we identify and respond to incidents?
First, it’s important to differentiate between a vulnerability and an incident. A vulnerability is a flaw that could potentially be exploited, where an incident is an actual exploitation or compromise of a system.
Of course, once something bad has happened on your network, responding appropriately must be a priority. All cybersecurity programs are measured by how quickly the organization can measure and respond to incidents, because the quicker the programs can eliminate the malware, the less damage is likely to be done. Unfortunately, many companies let malware dwell on their network for far too long, which allows the hackers greater opportunities to compromise their systems. This is often because the organization isn’t aware of the intrusion in the first place.
There are a number of different ways to measure incident response rates. You can:
- Use a security ratings provider like Bitsight to get actionable data about an incident right away.
- Identify a security incident on your system, shut it down, and manually record your own response time.
- Learn about an incident through a third party, such as law enforcement, and find out through them when an incident occurs based on their information.
Many organizations use a combination of their own internal processes and external resources for quantitative measurement. Regardless, the more visibility you have into your network, the better you’ll be able to monitor this metric. Once you’ve monitored this successfully, you can benchmark your remediation time and compare it within your organization historically and to your peers.
16 At-a-Glance Cybersecurity KPIs to add to your dashboard
16 At-a-Glance Cybersecurity KPIs to add to your dashboard
3. Do we have any outstanding high-risk findings open from our last audit or assessment?
This is another great commonly used metric in the area of security. Whether your last cybersecurity audit or assessment was done in-house or by a third party, it will typically include a number of recommendations in regards to improving your organization’s cybersecurity posture. The recommendation from the audit committee is almost always to patch any high-risk findings immediately. If any of the high-risk audit findings have not yet been completed in the time frame recommended, your board members should absolutely know about them.
4. Patching Cadence
This metric involves determining how many vulnerabilities you have in your system and how many critical vulnerabilities have yet to be patched. To understand the importance of patching cadence, consider software. When a new update comes out for a system you already have in place — or when you purchase a new software solution — it may have bugs or vulnerabilities that are found post-deployment. Patches for these vulnerabilities become available regularly — but they don’t do any good unless they’re applied immediately. Thus, frequent patching cadence can reduce the number of vulnerabilities in your system.
Conclusion
These commonly used metrics in the area of security are a great way to demonstrate the effectiveness of your cybersecurity program to the board or senior leadership. They both speak to the impact on the business and use metrics that will be commonly understood. To find cybersecurity kpi examples to include in your next report, or add to your cybersecurity dashboard, check out the guide below.