New! The Security Ratings report is now the Executive Report. Request your report to see enhanced analysis such as your rating, likelihood of ransomware incidents, and likelihood of data breach incidents.

Over the past couple of weeks, a major issue has surfaced affecting numerous companies that use MongoDB to store their data. Those who install MongoDB on a server and use default settings are exposing their data to the internet and allowing anybody to browse the databases, download information, and erase them entirely. Many companies are unaware of the vulnerability and that their information may be exposed to hackers. Criminals are reacting quickly and opportunistically by stealing data, then asking for a ransom. To make matters worse, some criminals asking for a ransom don’t actually have the data, so when the ransom is paid, companies are still left without answers. In addition to MongoDB, it was reported that clusters of Elasticsearch, an enterprise search engine has also been hit with ransomware.
Who Uses MongoDB?
How secure is your organization?
How secure is your organization?
According to Brian Krebs, there are over
52,000 of these publicly accessible databases on the Internet, and that figure may continue to grow as researchers discover additional
databases. The important question
is this: how many companies are potentially exposed to this vulnerability? To provide perspective, I used
our Bitsight Security Ratings platform and analyzed a sample of 1,870 companies across 14 different industries. I found that 112 (5.9%) of the companies from my sample were found having MongoDB exposed to the internet.
It’s important to note that just because a company is using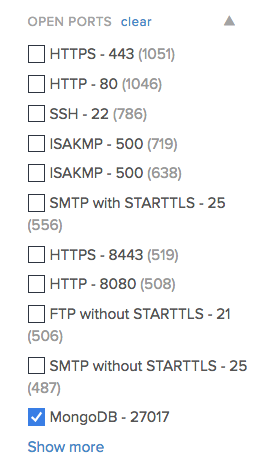
MongoDB, it does not necessarily mean that they’ve been the victim of an attack or that they are susceptible to one. Some companies may have configured their systems correctly by changing the default password and their sensitive information is not exposed over the internet. To investigate further, companies should seek to answer an important question through their security assessments: do you expose private information over the internet?
The Potential Impact
Whether a company uses MongoDB or another online database platform, if they expose sensitive information over the internet, they become vulnerable to cyber attacks. A recent study between Bitsight and Advisen, Bridging the Gap: How Cyber Practices & Data Breaches are Connected, found that 60 percent of breached organizations had 10 or more ports susceptible to unauthorized use. As we’ve seen with the recent MongoDB vulnerability, open ports exposed to the internet can provide ways for attackers to access a company’s network and steal information. The figure below from the referenced report shows the difference in performance between companies by the number of ports exposed to the internet.
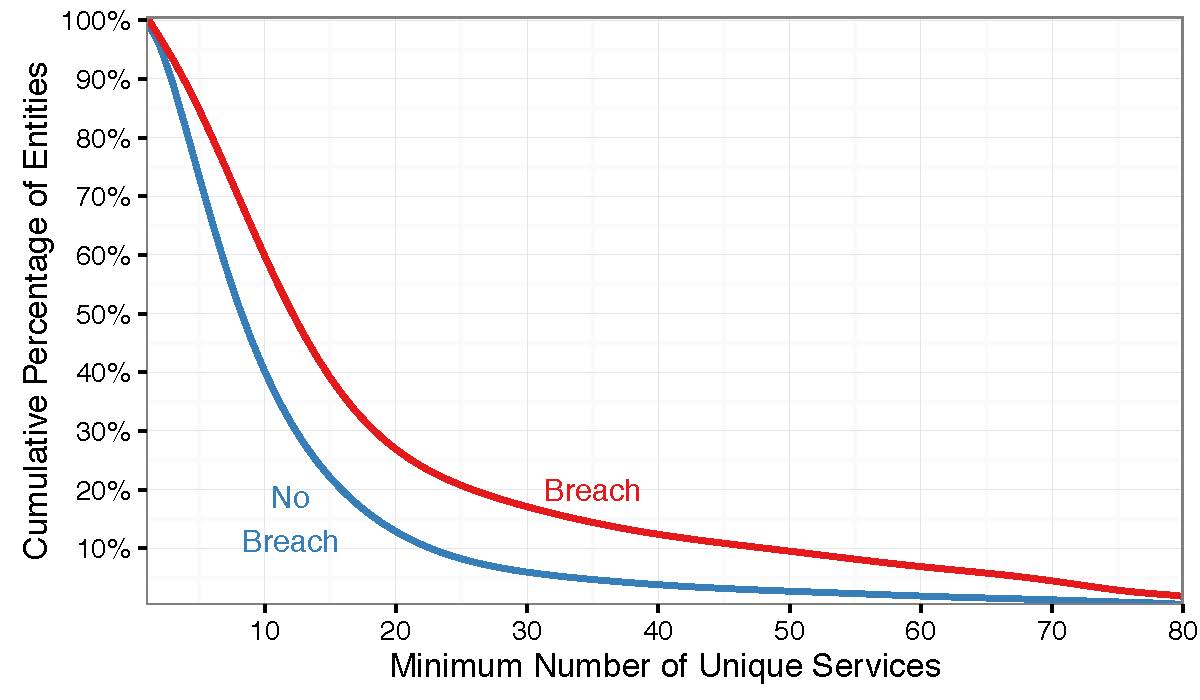
The issue of open ports and risk aggregation is especially important for cyber insurers with a large book of business. One single data breach or disruption that impacts many companies can lead to an influx of cyber insurance claims, which ultimately can have an adverse impact on a cyber insurer’s bottom line. According to Jake Olcott, VP of Strategic Partnerships at Bitsight, “insurers are concerned that one bad cyber risk can impact their entire book of business, so they are trying to understand what those risks might be and address them during the underwriting process.”
What To Do Next
Many companies are trying to figure out what to do in light of the recent cyber attacks stemming from the MongoDB vulnerability. There are some key steps that companies can take to mitigate the cyber risk of open ports:
- Backup Critical Data. Companies should perform backups of their data to ensure that if their information is stolen, they have systems in place to continue business operations.
- Properly Configure Servers. Companies should ensure that servers with sensitive information are not open to the internet. They should reconfigure these systems to protect their company’s private information. If you must access the data over the internet, you should restrict access to only internal users on VPN. As a quick first step, ensure that you change the default passwords on these servers.
- Continuously Monitor Third Parties. Companies may have their systems configured correctly, but their vendors may not. Organizations that emphasize good cybersecurity should hold their vendors to the same standards, and continuously monitor their security performance.
Bitsight enables organizations to search their book of business or folders of vendors and identify services such as MongoDB that are being exposed to the internet. Security teams can instantly generate reports showing the companies using these services, and send them an Enable Vendor Access request through the portal to provide them access to their own instance of Bitsight Security Ratings. Schedule your demo today!