New! The Security Ratings report is now the Executive Report. Request your report to see enhanced analysis such as your rating, likelihood of ransomware incidents, and likelihood of data breach incidents.

In today’s business world, the desire to transact in the digital realm is dramatically accelerating and, unfortunately, so is the cyber risk that one takes on as a result. Organizations that handle sensitive data are more likely to become the targets of hackers who are looking to exploit this information stored within their network. Businesses now find themselves exposed to a growing “Cyber Risk Gap.” This gap is the outcome of the combined impact of the following:
1. An increasing and changing set of risk/threat vectors.
Today, more than ever, there are innumerable ways for bad actors to penetrate business organizations. This was displayed over the past year with events like WannaCry and other ransomware attacks that caused business disruption as well as significant data compromise. Taking this into account, companies must be able to guard themselves against these increasing varieties/types of threats.
2. A higher volume of new vendors.
Organizations do business with more vendors than ever before — their ecosystem expands to include both their third parties and fourth parties. Subsequently, this means they take on the risk associated with these organizations — and there can be up to hundreds of thousands of these business partners. These third and fourth parties are liabilities because they have the ability to access your network, and vice versa. Today, the supply chain is fragmenting; it’s easier to do business online, and with that comes the threat of exposure to vendors’ networks that are not secure.
How secure is your organization?
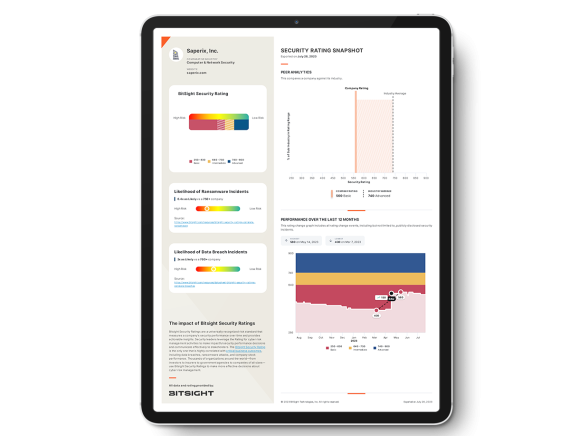
How secure is your organization?
3. A Cyber Risk assessment process that is labor intensive, qualitative in nature, and unable to scale.
When creating a risk management strategy, it’s most important to have assessment processes in place that can scale to meet the growing number of vendors that work with your business. Traditionally, assessment approaches like penetration tests and questionnaires are qualitative and episodic — they can only analyze risk at a certain point in time. While an important part of the risk management process, these labor intensive processes are not able to scale to meet the volume and timing requirements of the current risk environment.
It’s critical that organizations put into place assessments that are qualitative, quantitative, and continuous. Bitsight Security Ratings meet the critical emerging needs for continuous quantitative analysis to augment the episodic, qualitative assessments. While proactively mitigating risk, it’s crucial to have a standard measurement tool when looking at both internal and third party risk. Bitsight Security Ratings helps provide a quantitative measurement that reflects the dynamic nature of your business ecosystem: always changing and growing rapidly.