New! The Security Ratings report is now the Executive Report. Request your report to see enhanced analysis such as your rating, likelihood of ransomware incidents, and likelihood of data breach incidents.

A key factor in the widespread reach of the WannaCry ransomware attack earlier this year was that, prior to the attack, companies across hundreds of countries failed to apply a critical update (MS17-010) from Microsoft. This attack, along with the more recent NotPetya attack, has highlighted the prevalence and the risk of outdated software on corporate networks.
In a recent report, A Growing Risk Ignored: Critical Updates, Bitsight researchers found that over 2,000 organizations are running more than 50 percent of their computers on outdated versions of an operating system, making them almost three times as likely to experience a publicly disclosed breach. They also found that over 8,500 organizations have more than 50 percent of their computers running an out-of-date version of an Internet browser, doubling their chances of experiencing a publicly disclosed breach. As more devices connect into corporate networks, companies without robust endpoint security controls or mature third party risk management programs are more likely to experience cyber attacks in the future.
An Emerging Threat: Mobile devices
A 2016 survey from Gartner found that two-thirds of survey respondents used a personally-owned device for work. It is increasingly challenging for IT Security and Risk Management teams to monitor these devices and ensure that they adhere to the company's security controls. Given the probability of employees having sensitive company information on these mobile devices, monitoring the security of them, even if the devices are on guest Wifi, is extremely important. In fact, some security teams think that because a mobile device may be on the guest wifi instead of the corporate network, there is no reason to monitor the security of the device. However, they are overlooking the fact that these mobile devices may belong to employees with access to sensitive information, which means that if the device is breached, the information on that device could be exposed to hackers.
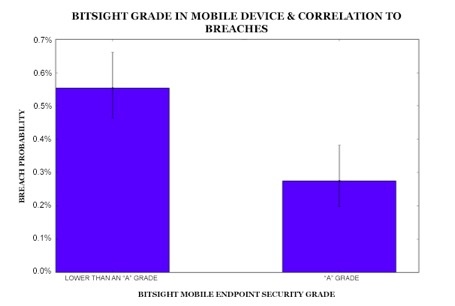
The increasing use of mobile devices is creating additional challenges for organizations - teams simply cannot scale with this level of growth and monitor the security of every new mobile device connected to their network. Considering how cyber criminals have exploited outdated systems to carry out massive attacks, outdated mobile devices may pose the next big cyber threat for companies. Bitsight researchers analyzed mobile endpoint grades for nearly 35,000 companies and found that organizations that have a mobile endpoint security grade lower than “A” are nearly twice as likely to experience a publicly disclosed breach than companies with an “A” (Figure 1).
Criminals are already developing malware, including ransomware, for mobile devices. For instance, McAfee researchers recently discovered LeakerLocker, a type of Android ransomware that makes a backup of data stored on a mobile device and threatens to share it with the user's contacts. Another example of mobile malware is XcodeGhost, a malicious code found in certain versions of Apple’s Xcode development environment that developers of iOS applications may inadvertently insert into their official iOS applications. Although these two examples are not directly related to outdated mobile operating systems or browsers, they demonstrate that cyber criminals are actively exploring ways of exploiting mobile devices to carry out successful attacks.
How secure is your organization?
How secure is your organization?
The risk from trusted third parties
Bomgar’s 2017 Secure Access Threat Report found that the average number of vendors accessing a company’s network has doubled in just one year to 181 per week, with 67 percent of companies experiencing a data breach because of unsecured vendor access. Given this finding and Bitsight’s discovery of a correlation between data breaches and high rates of outdated mobile devices, companies should strive to continuously monitor the endpoint security controls of their trusted third parties, especially those with access to sensitive information. The question ultimately becomes: are vendors doing enough to protect their business partners’ sensitive data?
The growing use of mobile devices in the workplace has added a new layer of complexity to securing endpoints and monitoring vendor security. Existing point-in-time vendor risk assessments, including questionnaires and onsite visits, should not be the only way of addressing the challenge. As a result, many organizations have begun to use technologies such as Bitsight Security Ratings to measure the security performance of their vendors and assess whether they are using outdated endpoints, including mobile devices, with outdated operating systems and Internet browsers.
As the digital world evolves and organizations expand their vendor ecosystems, organizations will find it increasingly important to monitor the security of the devices connected to their networks and the risks associated with trusted vendors. As recent ransomware attacks have demonstrated, outdated systems can lead to data breaches and cause major business disruptions, brand damage, and material loss. Companies should establish endpoint security controls and continuously monitor their trusted vendors to ensure that they adhere to the same standards.
Learn more about the relationship between recent ransomware attacks & endpoint security