
Australia has seen several high profile cyber incidents in 2023 and has seen significant loss of customer data (Canva’s 139 million customers, Latitude’s 7.9 million customers HWL Ebsworth’s 65 government agencies, 2.5 million documents).
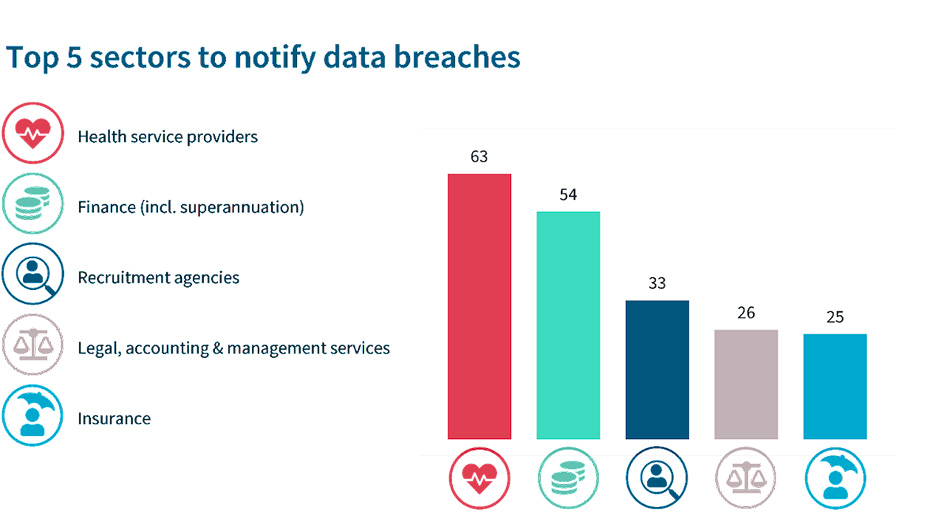
Source: OAIC Notifiable Data Breaches Report: January to June 2023
According to the OAIC Notifiable Data Breaches Report: January to June 2023, the top 3 sectors in that period to report data breaches are Health Service Providers (65 notifications), Finance incl. superannuation (54 notifications) and Recruitment Agencies (33 notifications). For an industry that is highly regulated, it is concerning that Finance (including superannuation) has the 2nd highest number of notifications submitted.
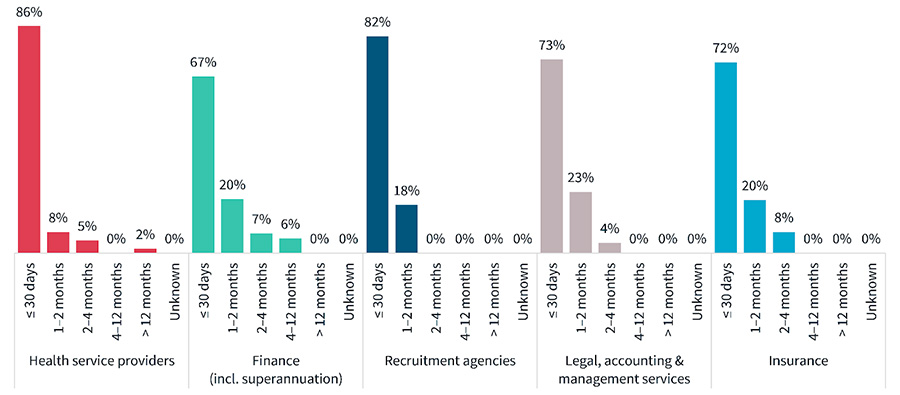
Chart: Time taken to notify the OAIC of breaches
What is also concerning is that 67% of the financial industry took less than 30 days to notify the OAIC, which by itself sounds fairly good, unfortunately when benchmarked against the other Top 5 sectors notifying the OAIC of breaches - Finance is ranked fifth and lowest of the Top 5. At fourth place is the Insurance industry at 72% notifying within 30 days.
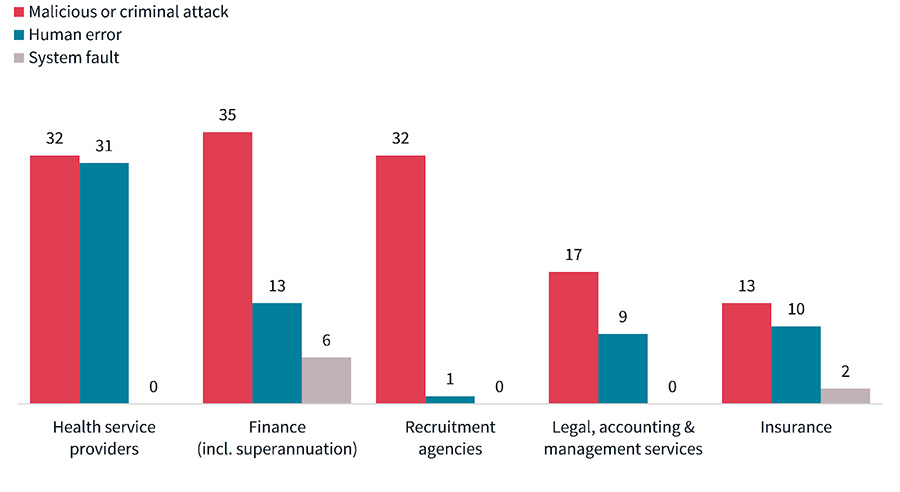
Chart: Source of breaches
The Finance sector is also listed in the same report as being the most often targeted by criminals and also the highest in data breaches resulting from system faults. At the point of writing, it certainly seems that the state of Cybersecurity in the Australian Finance sector leaves much to be desired.
The Australian Government had probably foreseen the cybersecurity gaps in the Finance industry when APRA (Australian Prudential Regulatory Authority) first released the CPS 234 as a draft in March 2018 (going into force in July 2019).
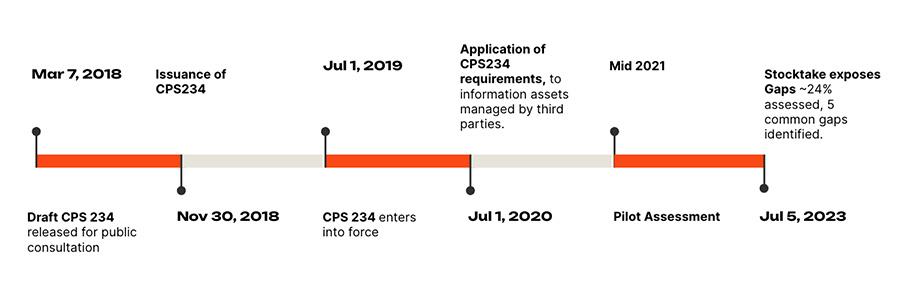
APRA has been diligently performing independent tripartite cyber assessment and by the end of 2023, more than 300 banks, insurers and superannuation trustees would have participated. By July of 2023, findings from the 1st tranche (~24% of APRA’s regulated entities) had brought to light highly concerning compliance gaps with CPS 234 standards among regulated entities. This further confirms the results of the initial pilot assessment reported in 2021.
It’d be unfair to say APRA regulated entities are negligent so what could be the possible reasons for this misalignment in expectations and state of compliance? What can businesses do about it? Let's explore the reasons behind these gaps and the hurdles faced by APRA-regulated organizations in fortifying their cybersecurity posture under CPS 234.
-
Making sense of CPS 234:
- CPS 234 is an information security regulation, and can easily land squarely (and solely) on Cybersecurity practitioners to lead initiatives to comply with the regulation. Cybersecurity leaders mostly prefer clear and concise requirements they can execute on (Essential Eight anyone?) regulations are often seen to be loose, and leaving too much room for interpretation. CISOs (or other cybersecurity leaders) are involved as subject matter experts to determine what the business need to comply with, how to comply and to what extent. As subject matter experts, CISOs are then tasked with building the necessary processes, implementing the required technology and building the business cases for CPS234 projects to the management / board. Adding to the challenge, the CISOs will likely need to navigate business processes and garner support from leaders for the “seemingly” needed initiatives.
- CISOs should see themselves as a Business Leader. By looking at opportunities, risk and constraints through business lenses, the CISO will be able to bridge the communication gap and transform the cybersecurity cost centre into a profit centre. Start by understanding the organisational goals, and design the cybersecurity investment strategy in accordance with the developing business landscape (moving to cloud isn’t always the answer). Being able to provide assurance is a hallmark of a well governed business.
- CPS 234 is an information security regulation, and can easily land squarely (and solely) on Cybersecurity practitioners to lead initiatives to comply with the regulation. Cybersecurity leaders mostly prefer clear and concise requirements they can execute on (Essential Eight anyone?) regulations are often seen to be loose, and leaving too much room for interpretation. CISOs (or other cybersecurity leaders) are involved as subject matter experts to determine what the business need to comply with, how to comply and to what extent. As subject matter experts, CISOs are then tasked with building the necessary processes, implementing the required technology and building the business cases for CPS234 projects to the management / board. Adding to the challenge, the CISOs will likely need to navigate business processes and garner support from leaders for the “seemingly” needed initiatives.
-
Dynamic Cyber Threat Landscape:
- The threat landscape is growing increasingly sophisticated, existing exploits (i.e. phishing techniques) are being creatively abused, and Generative AI is being leveraged for incredibly convincing hooks. Did you hear about the finance worker who paid U$25 million after be convinced in a deep fake meeting? Attackers have also been incredibly quick to exploit zero day vulnerabilities, Palo Alto reported hacks scanning for vulnerabilities within 15 mins of disclosure. Adding on, vendors that you would rely to protect could also be the ones to let the bad actors in (i.e. Cisco, Barracuda, Sonicwall, Fortinet…). Let’s not even start the conversation of Cloud security. Time is of the essence, the velocity of zero day vulnerabilities being released / announced can easily overwhelm cybersecurity teams. Being on top of your attack surface and the ability to prioritise remediations and patches
- Being able to establish a sound cybersecurity strategy provides a good foundation to defend against attacks. This does not mean building a castle (as we all know by now), but being able to identify, detect, protect, respond, recover to attacks (familiar?) and be resilient against attacks. Rather than a best-of-breed environment, a “lesser” integrated toolbox to be able to respond quickly. Instead of best of breed,
- The threat landscape is growing increasingly sophisticated, existing exploits (i.e. phishing techniques) are being creatively abused, and Generative AI is being leveraged for incredibly convincing hooks. Did you hear about the finance worker who paid U$25 million after be convinced in a deep fake meeting? Attackers have also been incredibly quick to exploit zero day vulnerabilities, Palo Alto reported hacks scanning for vulnerabilities within 15 mins of disclosure. Adding on, vendors that you would rely to protect could also be the ones to let the bad actors in (i.e. Cisco, Barracuda, Sonicwall, Fortinet…). Let’s not even start the conversation of Cloud security. Time is of the essence, the velocity of zero day vulnerabilities being released / announced can easily overwhelm cybersecurity teams. Being on top of your attack surface and the ability to prioritise remediations and patches
-
Navigating Complex IT and Business Environments:
- IT environments can be highly complex and sensitive environments, and implementing changes can be risky business. That’s the reason why whole books are written about IT change management, but complying to regulations does not equate to an overhaul nor an entire migration. Even then, there could be unknowns in an environment that would turn out to affect business operations. Inventorization is the natural next step but how long would this take, how much would you really uncover and at what cost? The uncertainty impedes the progress of compliance. So what should we do?
- Instinctively, we all want to know the whole picture before making decisions. The challenge here is, oftentimes, decisions are procrastinated with the lack of information as the reason, resulting in decision paralysis and progress is stalled.
- IT environments can be highly complex and sensitive environments, and implementing changes can be risky business. That’s the reason why whole books are written about IT change management, but complying to regulations does not equate to an overhaul nor an entire migration. Even then, there could be unknowns in an environment that would turn out to affect business operations. Inventorization is the natural next step but how long would this take, how much would you really uncover and at what cost? The uncertainty impedes the progress of compliance. So what should we do?
-
Resource Limitations:
- Resource limitations (think Budget, Time and Manpower) are a common challenge across any organisation, across any business unit and not unique to Cybersecurity. Cybersecurity’s challenge is exacerbated by the limited pool of talent available for hire, limited understanding of the technology and tight timelines and high frequency of distractions (think 0 day vulnerability announcements). CISO’s must become business leaders and priorities, determine what is crucial and demands immediate action and what can be managed at a later time. Resource allocation skills are important for the business leader, making the best use of resources to achieve business goals will create success.
- Being able to measure success in a quantifiable way would be the key, measuring reduction in risk in an objective sustainable manner is one way, or even better - reporting in dollars via financial exposures will help put in perspective where priorities should lie with the Board.
- Resource limitations (think Budget, Time and Manpower) are a common challenge across any organisation, across any business unit and not unique to Cybersecurity. Cybersecurity’s challenge is exacerbated by the limited pool of talent available for hire, limited understanding of the technology and tight timelines and high frequency of distractions (think 0 day vulnerability announcements). CISO’s must become business leaders and priorities, determine what is crucial and demands immediate action and what can be managed at a later time. Resource allocation skills are important for the business leader, making the best use of resources to achieve business goals will create success.
-
Third-Party Risks and Supply Chain Vulnerabilities:
- No business operates in the world alone today, we’re all interconnected into a closely knitted web of interdependence. The challenge is most companies do not know how many or who exactly they are connected with. Crucial vendors are easily identified and often monitored, unfortunately sometimes it’s the ones you aren’t concerned about that exposes you to a catastrophic event. Does anyone remember Target and their HVAC vendor who was the entry to the POS data theft? Being able to identify where you have crucial IT connections, or where your sensitive data is being processed or starred is just as important as implementing cybersecurity solutions to protect yourself. Remember, you can outsource a service but your CANNOT outsource the responsibility.
- Start by inventorying your vendors, determine what services they are providing, what data they are handling, are they easy to replace? Just a few simple questions can help you determine the rigour of assessment. It may seem daunting, but every step gets you closer to the end. Large businesses often have mature workflows, however weak tooling can often cause inefficiencies - oftentimes this gap is made up by tasking other full time employees with a part time vendor risk management responsibilities. Cycling back to resource limitations? Consider leveraging technology such as Vendor Risk Management platforms to introduce efficiency via workflow & automation. Leveraging data intelligence in the form of objective Security Risk Ratings may allow companies to much quickly determine inherent risks and work with vendors to reduce these risks to an acceptable level.
- No business operates in the world alone today, we’re all interconnected into a closely knitted web of interdependence. The challenge is most companies do not know how many or who exactly they are connected with. Crucial vendors are easily identified and often monitored, unfortunately sometimes it’s the ones you aren’t concerned about that exposes you to a catastrophic event. Does anyone remember Target and their HVAC vendor who was the entry to the POS data theft? Being able to identify where you have crucial IT connections, or where your sensitive data is being processed or starred is just as important as implementing cybersecurity solutions to protect yourself. Remember, you can outsource a service but your CANNOT outsource the responsibility.
-
Balancing Innovation and Security:
- Heard of the old adage “Convenience vs Security”, recent developments have made security much more simpler i.e. MFA apps or QR code scanners. Cybersecurity can often be misunderstood to slow down innovations because of the repetitive checks and depth that these checks can go into, stifling the “flow” of development. We are seeing for Innovations, seeing Security-by-Design frameworks are beginning to be adopted. And, in the realm of Application Development, this is brilliant. What about the rest of business operations and partnerships? Being able to enable the business to make informed decisions without having to pull the brakes for a full on cybersecurity assessment is important. Remember as Cybersecurity leaders, we want to enable the business. Although we can be seen as the brakes on a car, remember even the fastest F1 drivers need brakes to slow them down to take the fastest corners.
- Considering prevention, adopting and instilling a culture of cybersecurity, every member of an organisation can become effectively a cyber security endpoint and capable of providing some level of cybersecurity intervention. Considering, business velocity, being able to quickly perform pre-assessments and determine the rigour of assessment required (if at all) and translating this determination into a risk metric allows your decision makers to make the necessary calls with good assurance and confidence. You will then be helping to accelerate the business.
- Heard of the old adage “Convenience vs Security”, recent developments have made security much more simpler i.e. MFA apps or QR code scanners. Cybersecurity can often be misunderstood to slow down innovations because of the repetitive checks and depth that these checks can go into, stifling the “flow” of development. We are seeing for Innovations, seeing Security-by-Design frameworks are beginning to be adopted. And, in the realm of Application Development, this is brilliant. What about the rest of business operations and partnerships? Being able to enable the business to make informed decisions without having to pull the brakes for a full on cybersecurity assessment is important. Remember as Cybersecurity leaders, we want to enable the business. Although we can be seen as the brakes on a car, remember even the fastest F1 drivers need brakes to slow them down to take the fastest corners.
APRA's CPS 234 cyber security stocktake has really brought the challenges faced by regulated entities to light. As organisations strive to enhance their cybersecurity measures, it is crucial to consider the ever-changing threat landscape, the complexities of IT environments, resource limitations, third-party risks, and the delicate balance between innovation and security. Collaboration, continuous monitoring, and proactive strategies, guided by CPS 234, will be pivotal in ensuring a resilient defence against cyber threats for APRA-regulated entities. And hopefully, this same spirit goes on to infect the surrounding ecosystem and on and on, and at the the end of the day we see a stronger, more resilient Australia cyber world.
Noteworthy:
It may be misunderstood that all of the Finance (incl superannuation) industry is regulated by APRA, this is not true. Non-regulated financial industries include discretionary mutual funds, foreign bank representative offices, general insurance intermediaries, registered financial corporations, religious charitable development funds and wholesale funders. The list can be found here, these entities though not regulated would still be required to report to APRA.
Reporting by OAIC would include these non-regulated entities, but this would also highlight a blindspot when consumers or businesses assume ALL financial entities are regulated by APRA.