New! The Security Ratings report is now the Executive Report. Request your report to see enhanced analysis such as your rating, likelihood of ransomware incidents, and likelihood of data breach incidents.

The last couple of years have been tough on higher education systems in terms of cyber security. In 2012, in particular, there was a near-record-high number of data breaches, with nearly two million exposed records reported. The following year saw Maricopa Community College in Arizona experience a data breach that affected 2.4 million people. In 2014, there have already been several high-profile .EDU data breaches. In our latest Bitsight Insights report, we found that many universities are struggling to secure their networks due to unique IT infrastructure requirements and persistent security problems.
Obviously, these breaches come with costly consequences for these institutions. But what exactly is at risk? And who pays for these incidents? Hackers who target higher education systems aren’t looking to steal students’ transcripts and the targeted schools pay a high cost, with a lot more than money.
Why Target Schools?
Unfortunately, fewer than half of schools have a formal risk assessment and remediation program according to a recent SANS survey. Due to the open nature of campus networks that often have multiple access points, these networks are often left wide open for cyber attacks. In addition, university users are failing to stay alert when it comes to phishing scams and other threats. Hackers waste no time exploiting these weaknesses.
Even more worrying is the notion that many data breaches go undetected. Security risks are a constant threat, yet many university IT departments don’t have the resources to constantly measure security performance and to take the necessary precautions that would ensure the safety of their records databases.
What Is Taken?
So, if hackers aren’t aiming to get their hands on your perfect GPA, what are they hoping to gain? They’re looking to acquire crucial personal data that could do serious financial damage. As was the case with Maricopa, hackers can take social security numbers, bank account, and driver’s license numbers. Anything handed over to the institution is at risk for being stolen: health information, employee records, even valuable research.
How secure is your organization?
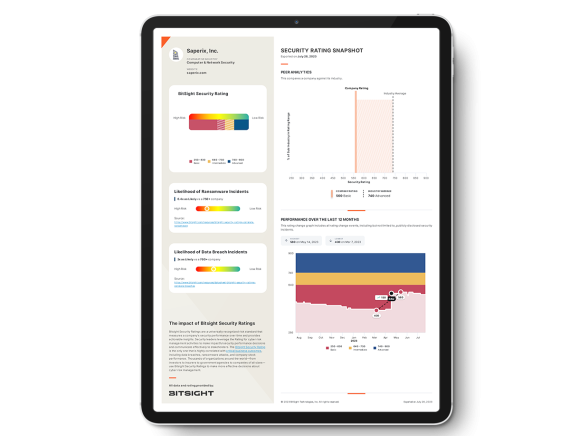
How secure is your organization?
What hackers do with this information can vary, but the most common result sounds straight out of the movies: They sell it on the black market. Credit card information isn’t the only hot commodity in the dark corners of the Internet. Anything relating to personal identity is considered valuable. In addition, many schools house research teams that are partners with government organizations and their contractors - making school systems targets of cyber espionage as well.
What Is the Cost?
A targeted higher education institution would see tangible expenses. For example, the Maricopa breach is approaching $20 million due to legal fees, repair costs, records management and consulting. And, according to a 2014 study by the Ponemon Institute, .EDU institutions can expect to pay around $259 per record stolen, behind only healthcare and transportation.
However, the cost can be greater than monetary losses. Timothy P. Ryan, director of the cyber investigations practice at Kroll Inc., told The Chronicle of Higher Education that the public only hears of about half of all university data breaches. This may be due to the fact that many institutions wish to safeguard their reputation. Nevertheless, it is likely that many of these breaches go undetected. So where can schools begin in addressing cyber security? With actionable and meaningful metrics, university security teams may be able to better identify and mitigate data loss. In addition, by communicating security performance to decision makers and benchmarking against peers, schools can allocate sufficient resources to address cyber threats. By taking these first steps, universities will begin to make the grade on protecting their valuable data.