Bitsight leverages our unparalleled data set to deliver differentiated insights to our customers. Our data and analytics deliver unique visibility to help organizations make better, smarter risk decisions.
Unparalleled data. Differentiated insights.
Bitsight leverages our unparalleled data set to deliver differentiated insights to our customers. Our data and analytics deliver unique visibility to help organizations make better, smarter risk decisions.
By the numbers
Independent, proven correlation to security incidents.
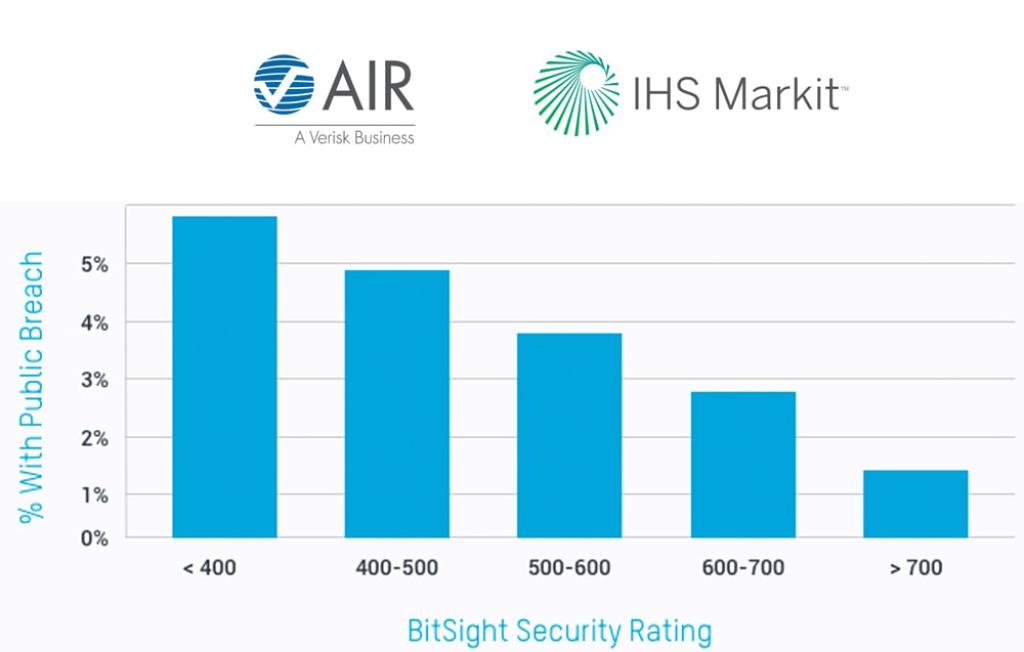
Independent, proven correlation to security incidents.
Bitsight Security Ratings represent more than just what’s happening on your attack surface. Bitsight takes program and vendor risk management a step further by offering companies an external and trusted view of network risks.
Our data is independently verified to correlate with an organization’s risk of a data breach. Confirmed by AIR Worldwide and IHS Markit, cybersecurity managers can rely on Bitsight data analytics to accurately summarize a program’s breach risk and better prioritize mitigation decisions with visibility into where the greatest risks lie.
See how Botnet infections correlate with breach risk.
Proven correlation to ransomware attack.
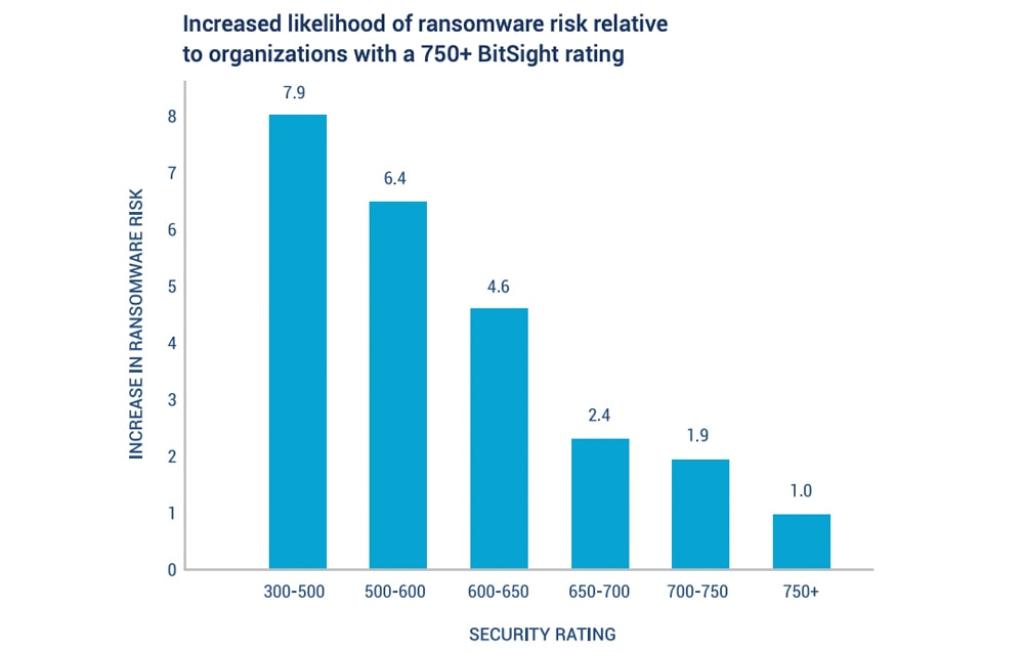
Proven correlation to ransomware attack.
Bitsight data is also directly correlated with the risk of a ransomware attack. As the rate of ransomware attacks grows globally, even the most well-established organizations are falling victim, and losing thousands or millions of dollars in the process. Bitsight data points to specific security gaps that are correlated with higher potential for ransomware attacks.
Armed with the data to tackle ransomware risks in your network, organizations can better protect their data, network, and reputation.
Significant correlation between Bitsight analytics and cybersecurity incidents.

Significant correlation between Bitsight analytics and cybersecurity incidents.
Marsh McLennan analyzed Bitsight security performance data across 365,000 organizations and its own proprietary cybersecurity incidents and claims database from 2018-2021, comparing the security performance data of thousands of organizations that experienced cybersecurity incidents against those that did not. The study concluded that poor performance in certain areas – including the Bitsight Security Rating and 13 risk vectors – increased an organization’s risk of experiencing a cybersecurity incident, while strong performance implied a lower risk of incident.
Independent, proven correlation to stock performance.
Independent, proven correlation to stock performance.
Bitsight’s encompassing pool of data has provided customers with a reliable tool to support cybersecurity decision-making. Security ratings are independently verified to correlate with an organization’s financial performance, according to independent Solactive research.
When directly connecting cybersecurity program decisions to a company’s financial performance, executives and board members can visualize the company-wide impact of a strong cybersecurity program.

"We were very confident in Bitsight’s ability to deliver accurate information to us and have that accuracy over time."
Our data sets us apart.
Building on the Principles of Fair and Accurate Security Ratings, Bitsight uses the below as a framework for our methodology and governance:
Security Ratings Data Categories
Compromised Systems
Compromised Systems
Compromised Systems are devices within an organization's network that are infected with malware. Each separate instance of malware communications, even if it is from the same machine, constitutes a single observation.
We identify and classify compromised systems into the following risk types:
- Botnet Infections
A unified network of machines that are performing coordinated actions based on instructions received from the malware’s creators. - Spam Propagation
Machines compromised with malware that causes them to send large volumes of unwanted email. - Malware Servers
A machine hosting a website that injects malicious code into a visitor’s browser, often resulting in the installation of new malware on that visitor’s computer. - Potentially Exploited
A machine running a potentially unwanted application which leaves the system vulnerable to adware, spyware, and remote access tools. - Unsolicited Communications
Any host that is observed trying to contact a service on another host that is not expected or supported.
Diligence
Diligence
Diligence records demonstrate the steps a company has taken to prevent attacks. We identify and classify diligence risk vectors as follows:
- Open Ports
- TLS/SSL Certificates
- TLS/SSL Configuration
- Web Application Headers
- Sender Policy Framework (SPF)
- DomainKeys Identified Mail (DKIM)
- Patching Cadence
- Server Software
- Desktop and Mobile Software
- Insecure Systems
- DNSSEC Records*
- Mobile Application Security*
- Domain Squatting*
* risk vector does not currently impact rating calculations
User Behavior
User Behavior
User Behavior examines activities that may introduce malicious software onto a corporate network, for example, by downloading a compromised file. We identify and classify user behavior into the following risk types:
- File Sharing
Media and software shared using peer-to-peer exchange protocols, which can be infected with malware. - Exposed Credentials*
Indicates whether employees of a company have had their personal or corporate information revealed as a result of a publicly-disclosed data breach.
* risk vector does not currently impact rating calculations
Public Disclosures
Public Disclosures
Bitsight collects information about publicly disclosed breaches and interruptions to business continuity from a variety of news sources and data breach aggregation services. A breach is attributed to a company when there is significant, publicly-disclosed evidence that the company was at fault for the data loss, such as a company-issued disclosure notice or investigation from a credit card company.

