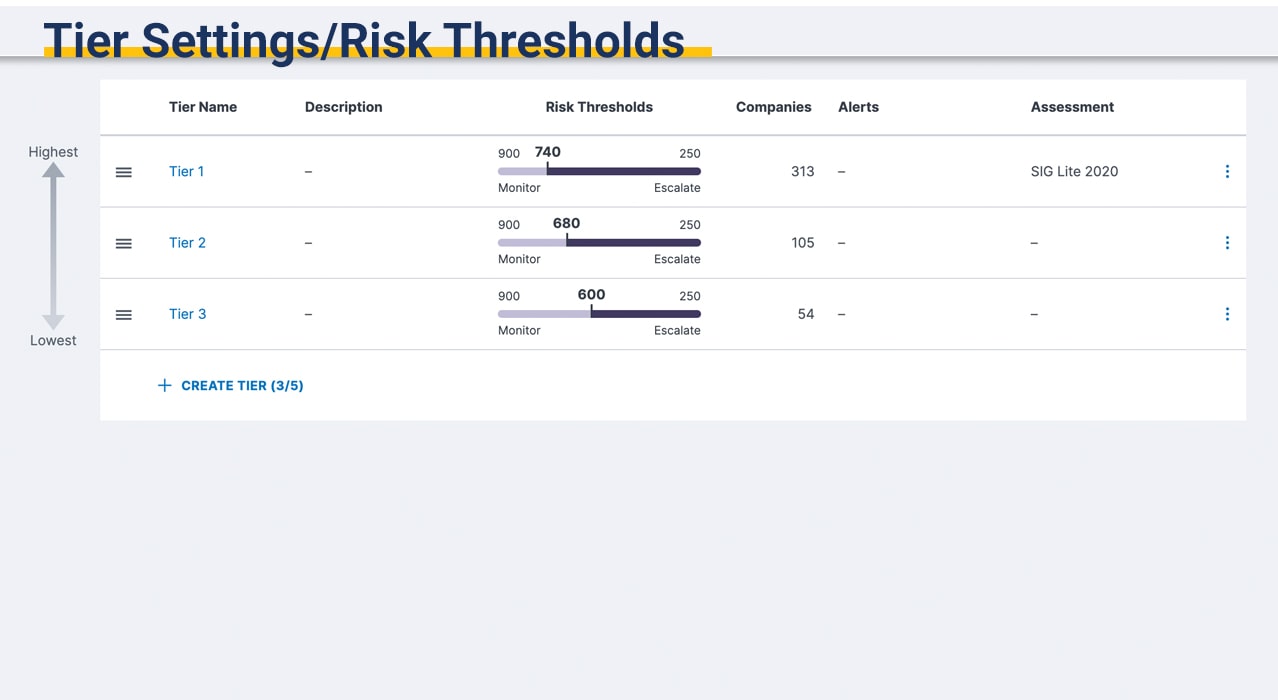
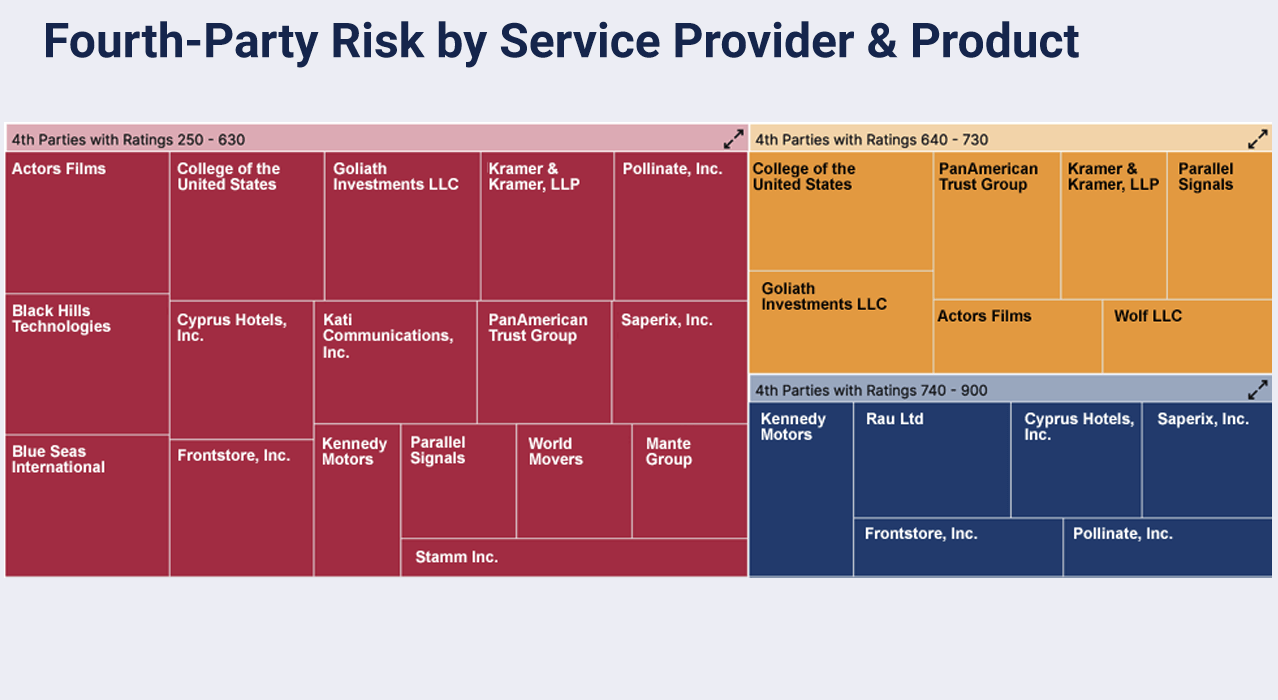
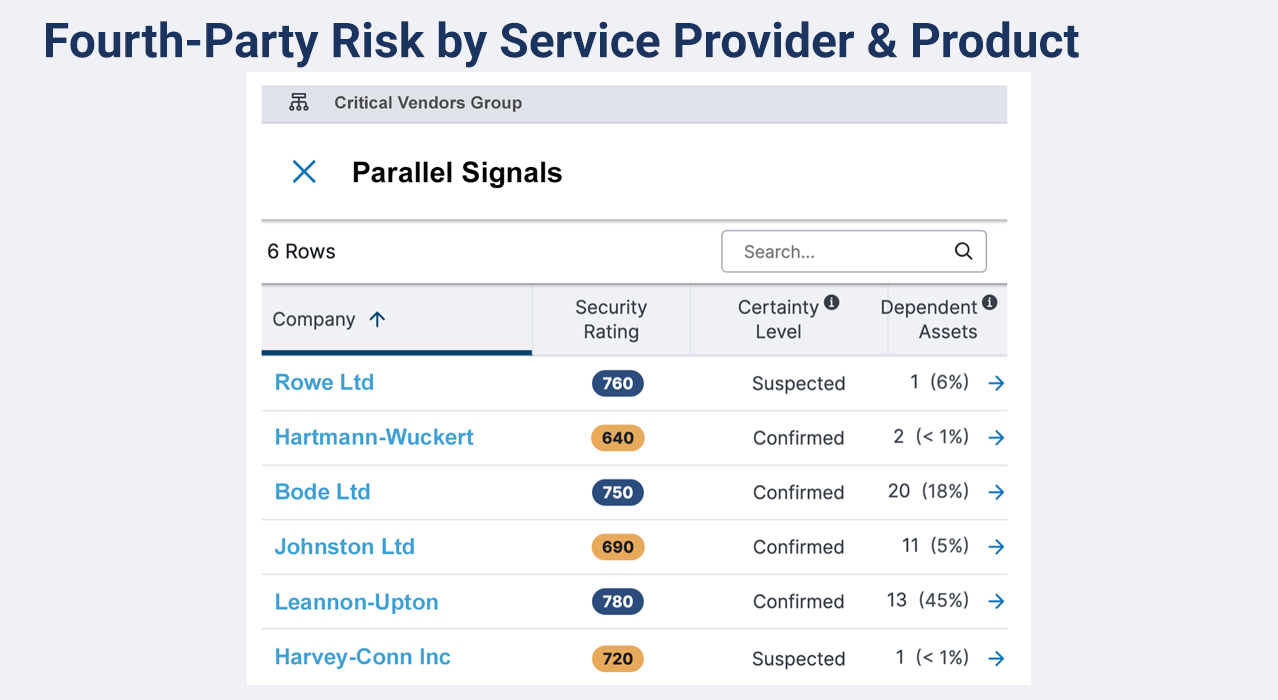
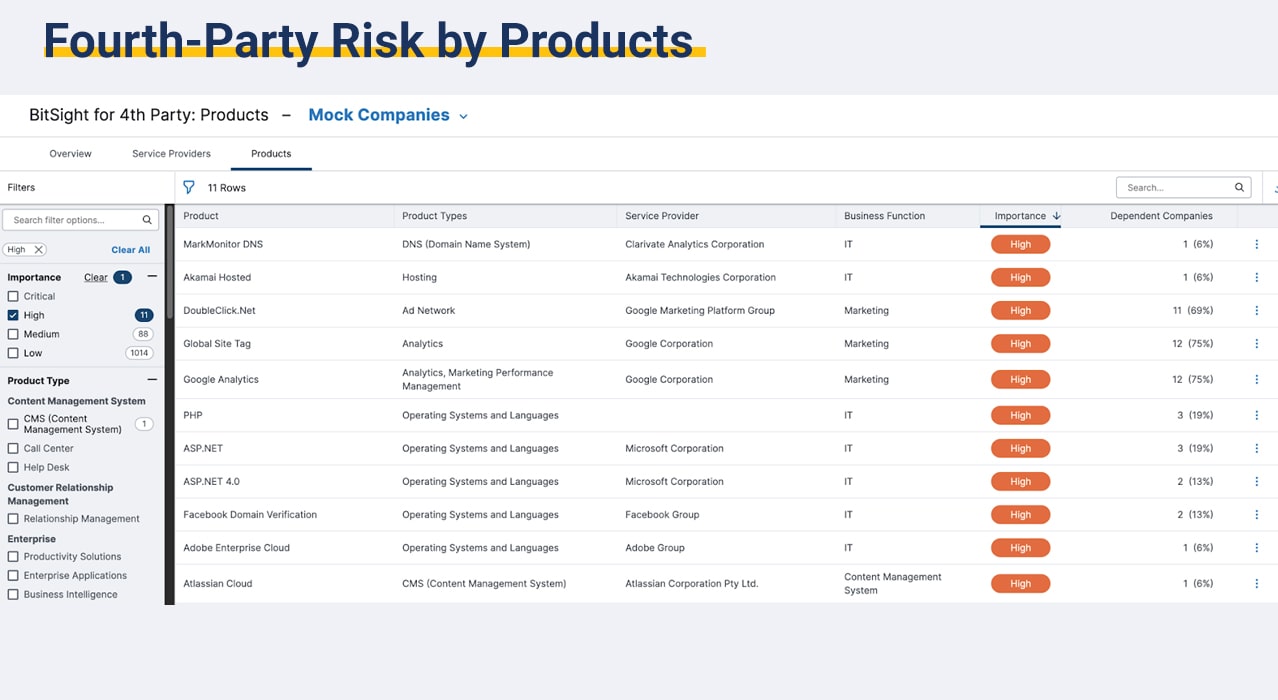
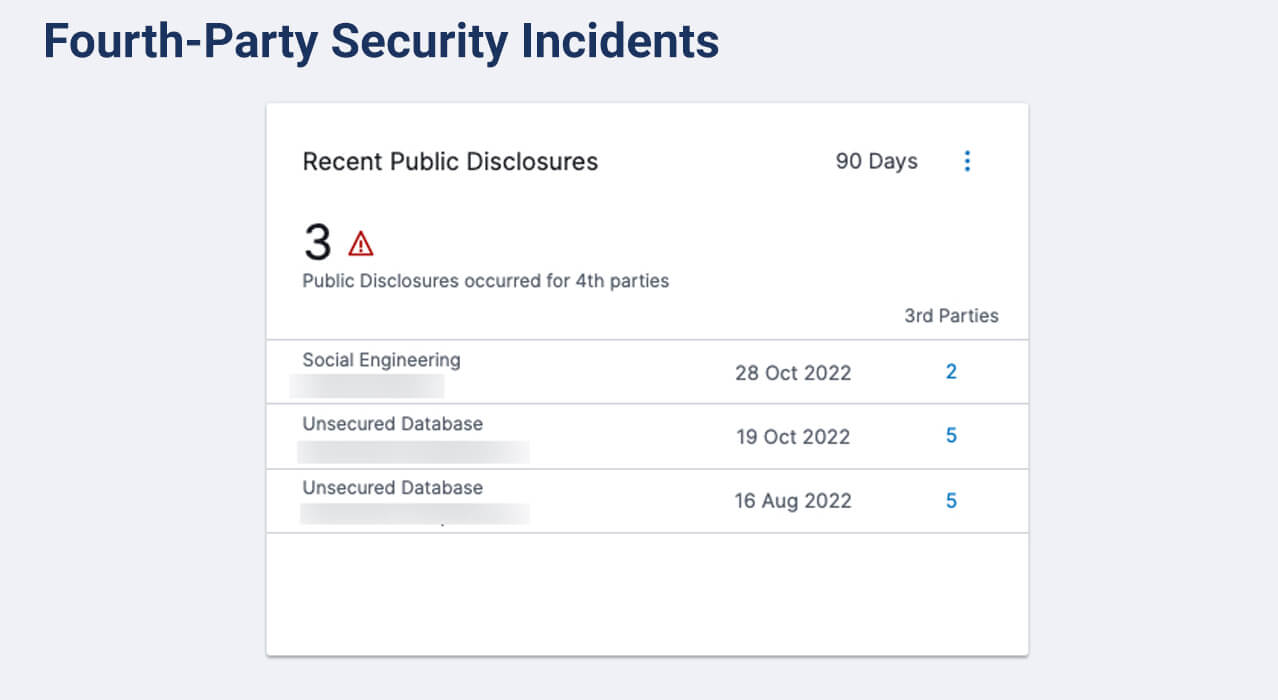
Manage the risk surface of your vendor supply chain with continuous monitoring.
Automatically identify vendor connections with other organizations, business partners, and potentially risky fourth parties in order to:
- Effectively validate security controls across your extended vendor portfolio
- Trigger alerts to security incidents in your extended vendor supply chain
- Gain visibility into the concentration of risk related to service providers and technologies